Priser og fakturering
Whitepaper XtraMile
Last Modified: 15.12.2025
The information contained in this document represents the current view of XTRAMILE AS on the issue discussed as of the date of publication. Because XTRAMILE AS must respond to changing market conditions, it should not be interpreted to be a commitment on the part of XTRAMILE AS, and XTRAMILE AS cannot guarantee the accuracy of any information presented after the date of publication.
This white paper is for information purposes only. XTRAMILE AS MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT.
XTRAMILE AS may have patents, patent applications, trademark, copyright or other intel- lectual property rights covering the subject matter of this document. Except as expressly provided in any written license agreement from XTRAMILE AS, the furnishing of this doc- ument does not give you any license to these patents, trademarks, copyrights or other intellectual property.
XTRAMILE AS, the XTRAMILE Logo, are trademarks of XTRAMILE AS in Norway and/or other countries. The names of actual companies and products mentioned herein may be the trademarks of their respective owners.
XTRAMILE AS, Sørkedalsveien 8c, 0369 Oslo
This white paper is for information purposes only. XTRAMILE AS MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT.
XTRAMILE AS may have patents, patent applications, trademark, copyright or other intel- lectual property rights covering the subject matter of this document. Except as expressly provided in any written license agreement from XTRAMILE AS, the furnishing of this doc- ument does not give you any license to these patents, trademarks, copyrights or other intellectual property.
XTRAMILE AS, the XTRAMILE Logo, are trademarks of XTRAMILE AS in Norway and/or other countries. The names of actual companies and products mentioned herein may be the trademarks of their respective owners.
XTRAMILE AS, Sørkedalsveien 8c, 0369 Oslo
CONTENTS
- Introduction
- Intended audience
- Basic overview of the XTRAMILE architecture
- General communication security
- Unauthorized online access prevention
- Password recovery
- Data import
- Server and network integrity
- Service uptime
- Backups and data redundancy
- Disaster recovery
- Security breach investigation
- Subcontractors
- Information collection
- User-created content protection
- Handling financial transactions and details
- Statutory body and regulation compliance
1. Introduction
What is included in this document?
Security is a top priority for XTRAMILE AS and its employees, just as it is for our clients. For this reason, we’ve had this issue in mind ever since we started to plan and design this service back in 2013. Thanks to this security-centric approach, XTRAMILE conforms to all current best practices of our industry.
The following whitepaper provides an overview of the safety mechanisms we have implemented in order to ensure the integrity of our sys- tems and services. It outlines security measures used during various steps of the user’s workflow, and outlines some crucial procedures, such as disaster recovery or security breach investigation.
What is not included?
Some internal/sensitive features are not described in detail, in order to deter potential attackers. Additionally, some details may have been minimized to protect our intellectual property (IP) rights. XTRAMILE operates in a competitive environment, therefore we are unable to dis- close some confidential details to parties that have not signed confidentiality agreements with XTRAMILE AS.
We ask you not to copy, distribute or reproduce this document without permission.
2. Intended audience
This paper is intended for the following audiences:
- IT managers and system administrators who are interested in the
security of XTRAMILE AS - Network administrators who are interested in the network / communication aspects of XTRAMILE AS
3. Basic overview of the XTRAMILE architecture
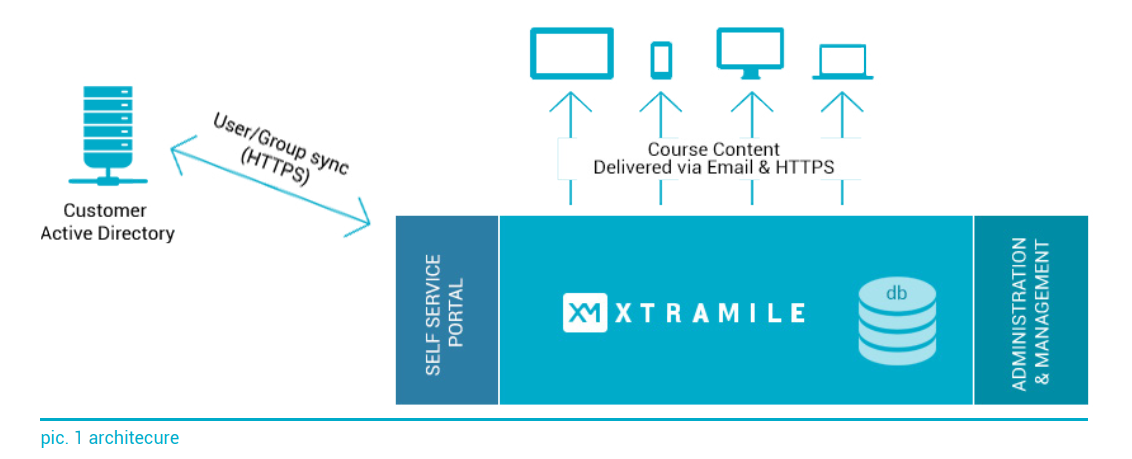
How does our platform work?
XTRAMILE is an innovative online training solution that vastly improves the information retention and ensures a deep, measurable change with- in client’s organization through a unique multi-step learning process.
XTRAMILE guides training participants through a list of pre-course activities, carefully tailored training modules, as well as post-course surveys and analysis. All relevant content is either delivered directly to user’s verified email, or provided by our web service and securely ac- cessible using many types of devices and operating systems.
We offer carefully crafted, optimized training modules for many common organizational needs, but we also enable our institutional clients to set up their own custom training projects. To facilitate bulk content upload and user account creation, our business partners receive special direct WebService token-based access or possiblility to synchronize using Microsoft Azure Active Directory.
The entire software and hardware infrastructure of XTRAMILE AS is built according to best security practices and diligently maintained.
4. General communication security
How do we encrypt our transmissions?
All online connections with XTRAMILE are made over HTTPS/SSL with certificate provided by GeoTrust Global and Google Trust Services.
The communication is secured using an asynchronous 4096 bit key with the 1.2 Transport Layer Security (TSL) encryption. We use the SHA256 RSA algorithm and the DHE_RSA key exchange mechanism.
The HTTPS/SSL encryption is a de facto standard for transferring pri- vate information on the internet and is being used in a variety of se- curity sensitive applications including internet banking, financial operations and leading e-commerce solutions such as eBay or Amazon Store.
To ensure highest possible security standards, we do not allow plain HTTP (unsecured) connections, even though it prevents some types of browsers and devices from interacting with the XTRAMILE platform.
5. Unauthorized online access prevention
How secure is our login system?
As mentioned in the initial overview of our architecture, XTRAMILE offers three ways for users to access their training content and accounts.
A. Online login
The web access to XTRAMILE is only possible after logging in, and mandatory HTTPS/SSL encryption makes it almost impossible for a hacker/cracker to successfully perform a so called “man-in-the-middle attack”.
All passwords used in XTRAMILE are required to meet a minimum safety standard:
- 8 characters
- At least one number and at least one letter
- At least one special character
This approach means that the minimum search space for an XTRAMILE password is equal to 109 505 194 890 (1.10 x 1011) combinations. We’ve also implemented a sub-second login delay, that limits the fre- quency of login attempts, while keeping the user experience unaffected. Therefore a brute force online attack would require up to three hundred years to succeed, assuming 10 guesses per second. Once the user is logged in, his session terminates automatically after a period of inactivity. The session ID is not displayed in the URL, and session access is controlled via browser cookie.
How does our token system work?
B. E-mail URL token
To make it easier for corporate users to quickly join training activities, we also offer a token-based system, whereby a user receives an e-mail invitation containing an active login link from the organizational admin. The link can only be used by people who hold an active XTRAMILE account that is authorized to view this specific training module.
The one-time login URL deactivates after a period of time and works only for a small number of entries, to make sure it’s not misused.
How does Single Sign-On work?
C. Azure Single Sign-On (SSO)
For corporate users which already are using Microsoft Azure Active Directory, we offer possiblity to login to our platform using Single Sign-on (SSO). When user provides his corporate email address on login page he is redirected to his corporate authorization service where he login with his corporate credentials.
6. Password recovery
A password recovery functionality is provided to users via their specified e-mail account. After entering a correct e-mail, we send out a link with a one-time secure access token. The link deactivates after a short period of time to limit the possibility of unauthorized use.
7. Data import
How do we enable safe data synchronization?
We support sync with remotes Active Directories to enable institutional clients easier bulk data uploads and account management. It’s possible to do this in two ways.
A. Local Active Directory connection
The communication with local client Active Directory is secured with a 64-bit secret key and a token unique to this specific client.
Should a client loose his token, or discover it has been accessed by unauthorized personnel, we offer a 24/7 direct contact number (+47 23 68 77 11) and we are prepared to immediately revoke remote access rights, until a new token is issued to an organization.
We also reserve our rights to revoke remote access and contactorganization’s administrators wherever our own staff or server logs provide a well-founded suspicion that the remote channel’s security has been compromised.
B. Azure AD connection
It’s possible to setup connection between XTRAMILE platform and client Azure AD by XTRAMILE support. This way XTRAMILE platform will be able to access client Azure AD and synchronize account informations.
8. Server and network integrity
How do we secure our platform?
XTRAMILE is using Microsoft Azure cloud to run it’s platform.
Azure is a cloud service platform that supports a broad selection of operating systems, tools and databases.
Azure offers you unique security advantages derived from global security intelligence, sophisticated customer-facing controls, and a secure hardened infrastructure. This powerful combination helps protect applications and data, support your compliance efforts.
Azure cloud is tightly secured to satisfy most regulatory or security requirements, including HIPAA, ISO 27001/27002, and PCI DSS Level 1.
To provide security XTRAMILE controls access to Azure environment by using:
- Firewall rules that limit connectivity by IP address.
- Authentication mechanisms that require users to prove their identity.
- Authorization mechanisms that limit users to specific actions and data.
- Azure Key Vault management service is used for storing systems cryptographic keys
- SQL Always Encrypted feature when we store sensitive secrets in the database
The internal infrastructure at XTRAMILE AS is proteted by MikroTik Cloud Firewalls. MikroTik is a company with very high reputation among security experts. It’s customers include HP, Ericsson, Motorola, Mitsubishi Motors, NASA and Siemens. This firewall provides an automatic DenialOfService attack detection and prevention systems, as well as many other automatic security features. We always use Azure VPN client when connecting to the Azure DB.
9. Service uptime
Backups and data redundancy.
How is your data backed up?
All critical infrastructure elements of XTRAMILE is running on Microsoft Azure cloud platform which has built-in secure database backup management features.
XTRAMILE database is using point-in-time restore (PITR) by automatically creating full backup, differential backups, and transaction log backups. Full database backups are created weekly, differential database backups are generally created every 12 hours, and transaction log backups are generally created every 5 - 10 minutes.
The backups are stored in RA-GRS storage blobs that are securely encrypted and replicated to a paired data center for protection against a data center outage. This ensures that the account details, history and other information of our users are kept intact even under most disastrous
circumstances.
11. Disaster recovery
How to contact us in case of an emergency?
In the unlikely event of a critical failure, XTRAMILE provides clients with
a 24/7 emergency contact line:+47 23 68 77 11
a 24/7 emergency contact line:+47 23 68 77 11
This number provides direct access to the members of our team, bypassing help-desk or any other customer service systems. If our team is unable to react in time for any reason, an automatic disaster recovery solution triggers overnight, attempting to fix irregularities with the help of the last hot backup.
It is important to note that due to meticulous testing and very high
standards of software development we haven’t encountered any total
system failures yet.
standards of software development we haven’t encountered any total
system failures yet.
The disaster recovery procedures are practiced and reviewed every 6
months.
months.
12. Security breach investigation
What do we do in case of a security breach?
Incidents that are classified by our team as security breaches (and therefore receive highest priority) include: theft or unauthorized access of information or sensitive data, any successful or failed attempts to compromise our network or server infrastructure, sudden loss of service, data corruption or serious system malfunctions, unauthorized use of our systems by any person, and any detected or suspect changes to any XTRAMILE AS hardware, firmware of software.
In any of the above events, reported by either client or our developers, we’re ready to immediately launch a procedure consisting of:
Identification – our experienced IT security personnel immediately reviews the log files, recorded events and details of server activity, running various incident-response tools when necessary.
Containment – the team makes sure no additional data or accounts can be compromised. This includes implementing stricter firewall rules as well as close coordination with client’s staff.
Eradication – our software engineers step in to roll back all unauthorized changes and restore the data and service integrity using one of the recent backups. Any passwords that could be accessed by the attacker are immediately flagged for replacement.
Recovery – systems are returned to regular service and monitored for any further activity
Lessons learned – we review the case, create an executive summary of the incident, identify root cause and determine ways in which the XTRAMILE platform might be improved. Security-related improvements are on top of our list of software development priorities.
13. Subcontractors
Who helps us with the development?
Our subsidiary company, Xtramile Gdansk, is doing the software development of the application in close cooperation with our norwegian team.
14. Information collection
What information do we gather?
XTRAMILE is tracking users activity only related to progress made in courses and lessons completed. We only gather basic access information such as browser language, version or device type. We do not use geotagging and the only cookies we leave on user’s device are related to his active session, our Google Analytics, Azure Application Insights and HubSpot research.
See our cookie police here: https://www.xtramile.no/personvern-og-cookies
15. User-created content protection
How do we protect our client’s data?
We do not review or intentionally access the content of training modules set up by our clients or their staff, unless the client specifically asks us for either technical or educational help. We believe our client’s training modules are strictly confidential and we use all available measures to limit the number of XTRAMILE developers or team members who can access any custom user-created content.
The customers remain in full control of the data throughout the entire process, and thus they are the only party responsible for quality, accuracy, appropriateness or intellectual property ownership of the content they upload to XTRAMILE.
16. Handling financial transactions and details
How do we handle financial transactions?
XTRAMILE web service and any of its modules do not contain any first party or third party payment processor / solution. We also don’t keep any financial data in our main XTRAMILE database. This greatly reduces the risk and the number of potential attack vectors.
We are mostly involved with big institutional and business partners, and that is why invoicing is handled outside of the XTRAMILE service, ensuring the best possible level of service, communication and security.
17. Statutory body and regulation compliance
What regulations are we subject to?
XTRAMILE AS privacy and data security policies are compliant with both Norwegian and European Union guidelines. All data and personal information of XTRAMILE AS clients, as well as any content created by them, always stays within our region.
We are determined to never voluntarily disclose any of our client’s data or any content of training modules uploaded to the XTRAMILE service, unless forced to do so by a valid court order from a Norwegian court, law enforcement officers or authorized governmental agencies.
Should such a request ever be made, we’re going to immediately notify any affected customers, detailing what type of data has been accessed.
